Threod Privacy Policy
Entering into force on 10th September 2025
1. Introduction and Purpose
The purpose of the present Privacy Policy is to provide data subjects (including You) with information about the data processing performed by Threod Systems AS, registration code 12323903, registered address at Kaare tee 3, Lubja küla, Viimsi vald, Harjumaa, Estonia and its subsidiaries, namely by Threod Defence OÜ, registration code 16935299, registered address at Kaare tee 3, Lubja küla, Viimsi vald, Harjumaa, Estonia related to its products and services (hereinafter Threod).
Please read this Privacy Policy carefully, as it contains information on how Threod processes personal data and on your rights as a data subject (hereinafter referred to as data subject/you).
We are committed to ensuring the lawful, fair, and transparent processing of personal data in accordance with:
- Regulation (EU) 2016/679 (General Data Protection Regulation, GDPR).
- Estonian Personal Data Protection Act (Isikuandmete kaitse seadus).
This Privacy Policy will explain and give You information regarding:
- the purposes of the processing and how your personal data is processed;
- on what legal grounds your personal data is processed;
- which personal data is collected and further processed;
- how long it is kept;
- how it is protected and safeguarded;
- who has access to your personal data;
- what are your rights and how you can exercise them;
- who to contact if you have questions or complaints.
This policy applies to all personal data processed by Threod Systems AS and Threod Defence OÜ, including that of our employees, business partners’ representatives, and any incidental personal data captured during testing of our products. This Privacy Policy does not govern all the processing of personal data in the employment relationship. Information on the processing of personal data by the Threod’s staff is provided in the internal documents of the company. Candidates for employment at Threod can read about the personal data processed during the application process at Section 11.
2. About Threod
Threod Systems AS owns the intellectual property rights of the IT and IP solutions of the Threod group and the trademark Threod. Threod Systems designs and manufactures Unmanned Aircraft Systems, electro-optic payloads, UAV launchers and their integration and other operation-critical sub-systems (hereinafter named as Products).
Threod Systems AS (hereinafter Threod) is the controller for the processing described in this Privacy Policy. This Privacy Policy is available to data subjects and other persons at www.threod.com.
On Threod’s social media pages, personal data is processed by the respective platform provider in accordance with the privacy policy of the relevant platform. Threod complies with this Privacy Policy when processing personal data. On social media, you should be aware that social media platforms process personal data in accordance with their own terms and conditions, which you can consult on the social media websites.
On Threod website, Threod may refer to links that take you to websites operated by third parties. If you click on any of these links, you will leave Threod’s website and be redirected to the website of that organisation or company. Although there may be a link between Threod and a third-party website, Threod has no control over the content of these websites or the processing of personal data on these websites. Each organisation is responsible for the processing of personal data on its own website. Before sharing personal data, we recommend that you read the privacy policy of the relevant website.
3. Categories of Personal Data Processed
Threod receives Your personal data from:
- Directly from You mainly in connection with employment in Threod and in connection with job applications;
- Directly by contacting Threod;
- From Threod’s website at www.threod.com;
- From Threod’s social media accounts in Facebook, YouTube and LinkedIn;
- From real-world Product testing through incidental images or video recordings that may capture natural persons;
- Through Threod’s security measures involving internal and external monitoring.
4. The purpose and legal grounds for personal data processing
Personal data is processed strictly in accordance with GDPR Article 6. The purposes and legal bases are listed below in table.
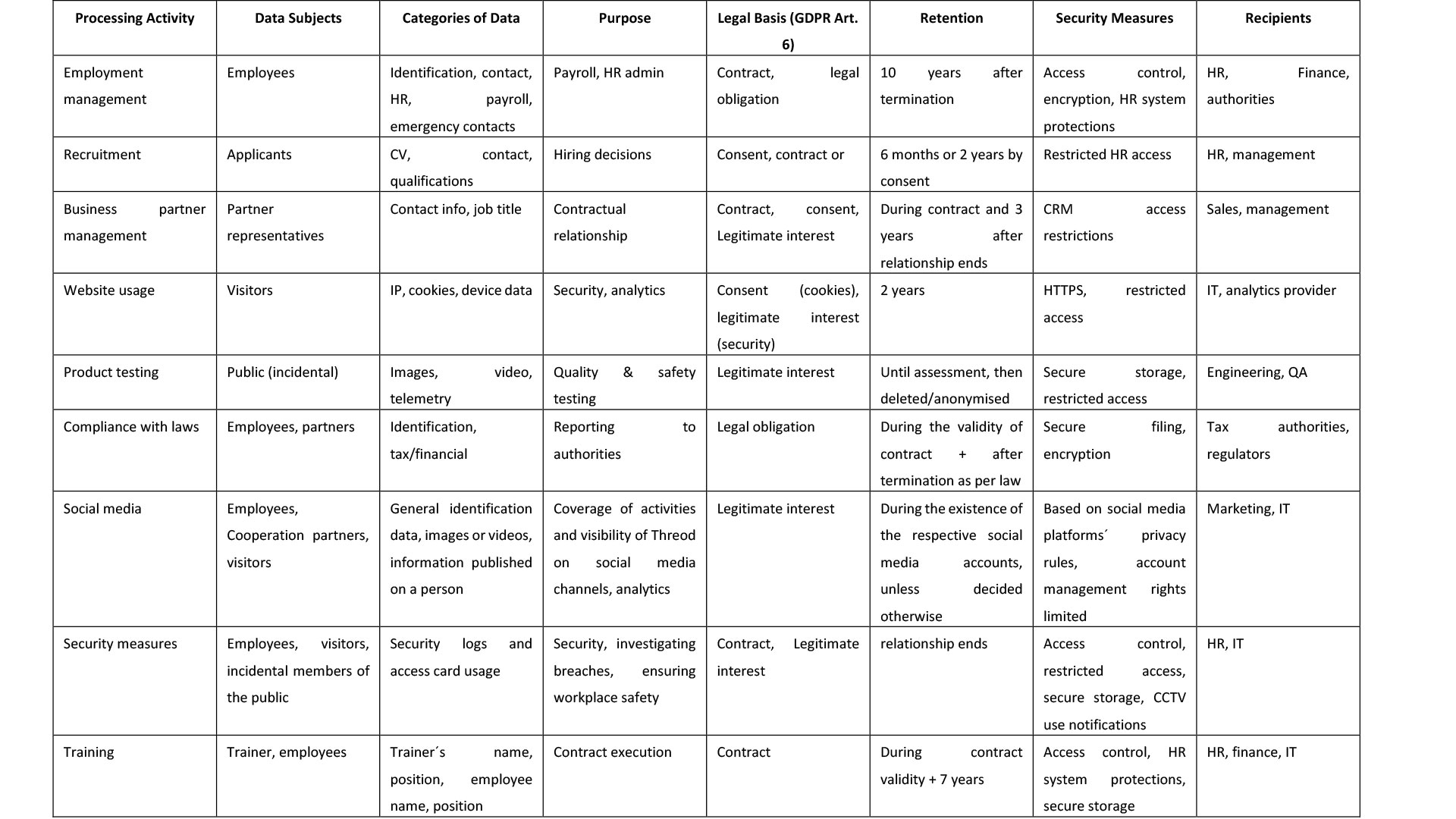
For all categories of data, the data processed will be the data necessary for the corresponding purpose and in the required volume processed only by Threod employees who need the personal data to fulfil their job function.
5. Retention Periods
Threod processes personal data for the purposes for which they are processed and does not process personal data for longer than necessary. To this end, Threod has set time limits for the storage of personal data, and we will only process personal data for as long as necessary for the purpose for which it is processed. The retention periods are mainly based on the obligations laid down by law and the protection of the interests of Threod and, in relations with Cooperation partners, inter alia, the limitation periods for possible claims. Generally, data will not be kept for more than ten years.
As listed in the table above the retention periods for categories of personal data are the following:
- Employee data: retained for the duration of employment and for up to 10 years after termination (statutory limitation period in Estonia for employment-related claims).
- Job applicant data: retained for 6 months after recruitment process unless the candidate gives explicit consent for a two-year retention period.
- Business contact data: retained for the duration of the business relationship and up to 3 years thereafter.
- Contractual and transaction related documents: retained up to 7 years after the end of the financial year during which the transaction occurred in line with accounting rules.
- Website analytics data: retained for 2 years.
- Incidental UAV testing data: stored only as long as necessary to assess product performance and deleted or anonymised thereafter.
- CCTV and incidental testing data: stored only as long as necessary for safety and deleted thereafter.
6. Data Protection and Security Measures
We use authorized processors bound by Data Processing Agreements (DPAs) to ensure compliance. Key processors include Persona, Microsoft 365, Stebby, Confido, Atlassian, and others. Data may be shared with banks, accounting providers, recruitment platforms, and competent authorities where legally required.
We use industry-standard technical and organizational measures to protect personal data, including:
- Encryption in transit (HTTPS) and at rest;
- Access control and authentication;
- Regular system monitoring for vulnerabilities;
- Employee training regarding data protection;
- Data processing agreements with all service providers in line with Art. 28 GDPR.
We implement for personal data protection the following technical and organizational measures:
- Authentication and 2FA;
- Backups and cloud data loss prevention;
- Encryption in transit & at rest;
- Access rights management;
- Logging & monitoring;
- Employee confidentiality agreements;
- Data Processing Agreements with processors;
- Secure local servers and restricted access rights.
7. Data Access and Sharing
7.1. Access to personal data is restricted to authorized personnel based on their role and job description. We share personal data only on a need-to-know basis bearing in mind that less is more and each use case needs legal basis and reasoning for processing.
7.2. We may share data with:
- Service providers (e.g., cloud hosting, IT support, payroll, analytics) under contractual safeguards.
- Authorities, where required by law or in response to lawful requests.
- Cooperation partners, where necessary for contract performance.
- Third-country partners only under adequate safeguards (see section 8).
7.3. In carrying out Threod´s activities, it may be necessary to transfer data to third parties. Where such transfer is strictly necessary for the performance of our activities, the relevant service provider will generally be our processor and will use the same basis of processing as ours.
7.4. Authorised processing. Threod may use service providers who are authorised processors of Threod. These processors are, inter alia, service providers who provide:
- IT services (document management system, IT maintenance, IT support, resale of MS Office services, purchase of workstation equipment, virtual server service, etc. – the scope of processing of personal data depends on the specific service provider and our respective needs).
- Accounting software (Accounting data).
- Accounting audit service (Accounting data, limited information on staff, Cooperation partners, etc.).
- Security service (limited scope of data on staff, candidates, Cooperation partners, etc.).
7.5. When transferring personal data to an authorised processor, Threod ensures that the processors process the personal data in accordance with Threod’s instructions, comply with confidentiality requirements and implement appropriate security measures.
7.6. Other processors.
Personal data may also be transferred to:
- Authorities and supervisory authorities entitled to receive the data.
- Other public authorities entitled to receive the data, such as investigative bodies, law enforcement authorities. Threod will consider the content and legitimacy of the request and will transmit the minimum necessary data.
- To processors providing payment services, financial service providers and financial institutions (in relation to the making of payments).
- Legal and financial advisors and other consultants. All personal data may be processed as necessary.
- Recruitment service providers (recruitment data of job applicants).
- Providers of postal services, telecommunications services.
8. International Data Transfers
8.1. Location of processing. Personal data is not generally transferred outside the European Economic Area (“EEA”). If a situation arises where it is necessary to transfer personal data out of the EEA, this will be done in accordance with the requirements of the GDPR (i.e. only to countries/institutions ensuring an adequate level of protection for personal data or using the EU standard clauses or other means permitted by the GDPR), including that the data may be transferred with the explicit consent of the data subject, provided that such transfer is essentially a one-off transfer at the request of and with the informed consent of the data subject.
8.2. The texts of the EU standard clauses can be found here. The list of the Data-Privacy Framework can be found here. Adequate protection has been recognised by the European Commission for the countries listed here.
9. Personal Data Security and Incidents
9.1. Security. Threod has established policies and procedures and employs a variety of organizational, physical and technical security measures to ensure the confidentiality and security of personal information.
- Organisational security measures: internal rules on responsibility for work processes, access rights, withdrawal of access rights at termination of employment, contractual safeguards to ensure confidentiality of information, internal rules of procedure communicated to staff upon entry into employment, record-keeping of equipment and software used to process personal data, access management systems, firewall, anti-malware (where appropriate), systems monitoring and testing.
- Physical security measures: Smoke detectors and extinguishers are installed in the premises. Physical access to the premises is restricted (door locked and keys and access cards managed, alarms installed and responded to by a security company). The position of the workstation, the physical layout of equipment and paperwork ensure that the eyes of unauthorised persons cannot wander too far and that there is no possibility of something being taken away unnoticed. Computer screens are locked when not in use. Papers containing restricted information shall be destroyed in the shredder.
- IT security measures: Back-up copies are made to protect against destruction of digital information. Users of digital information must be identifiable by name. Computer users are forced to change their password after a certain period. Removable storage media on the work computer are not allowed for staff.
- In addition, staff will be trained on information security and personal data protection issues and will use partners that comply with security requirements that meet industry market standards.
9.2. Threod has an incident reporting procedure. In the event of an incident involving personal data, Threod will do its utmost to mitigate the consequences of the incident and reduce similar risks in the future. Threod will follow the requirements of the GDPR when reporting an incident.
Among other requirements, the following rules are in place:
- All staff must report suspected breaches immediately to IT/Privacy contact at privacy@threod.com.
- Data breaches are assessed within 72 hours.
- Notifications to supervisory authority and affected data subjects as required by GDPR Arts. 33–34.
10. Your rights as data subject
You have the right to:
- Access your personal data;
- Rectify inaccurate or incomplete data;
- Erase data (“right to be forgotten”);
- Restrict processing;
- Object to processing (including legitimate interests);
- Data portability in a machine-readable format;
- Withdraw consent at any time.
To exercise your right please contact us at privacy@threod.com.
Before granting rights relating to your personal data, Threod may need additional information to identify you. We may ask for a digital signature on the application or, in the case of a handwritten signature, for the inclusion of identification (photo). This is to avoid that your data is issued to the wrong person.
Threod does not use profiling or automated decisions that would be in line with Article 22 of the GDPR. If Threod starts to use automated decisions or profiling within the meaning of Article 22 of the GDPR that have legal consequences or significant impact, Threod will inform the data subject and provide the data subject with the related rights – in which case the data subject will have the right to object at any time, on the basis of his or her particular situation, to the processing of personal data concerning him or her on the basis of automated decisions and profiling and to request human intervention. The data subject may also ask for an explanation of the rationale behind automated decision-making.
11. Personal Data of Job Applicants
During the job application process, we process your personal data to assess your suitability for the job and to implement pre-contractual measures and conclude the (employment) contract.
The processing of your personal data generally includes:
- Processing of personal data provided to us by you for the purpose of concluding an employment contract or similar contract (name, address, date of birth, gender, telephone number, e-mail address, photograph, CV, cover letters, application forms, documents relating to your skills and qualifications, references and letters of recommendation. The legal basis is covered by the contract in case of entering a contract with you and by your consent when you have provided the data yourself. When we use a recruitment service provider or contact you directly ourselves, we process your personal data based on legitimate interest. When you disclose a special category of personal data (e.g. in a CV) during the application process, the legal basis for your personal data processing is your consent Art. 9(2)(e) of the GDPR.
- Data for the assessment of the suitability of the candidate, for example a questionnaire by telephone or e-mail, test (if containing personal data), information disclosed at a job interview and the overview of the application process is processed based on performance of a contract Art. 6(1)b).
- When we run a background check, we do so based on your consent and/or based on legitimate interest.
- We may use recruitment service providers and software in the recruitment process. Depending on the recruitment service, the first contact may be based on consent or our legitimate interest when we contact you directly.
- If a you are not chosen for the job, we may retain the your personal data based on your consent to make you an offer of employment in the future if a suitable position becomes vacant.
12. Supervisory Authority Contact (Estonia)
Andmekaitse Inspektsioon
Address: Tatari 39, 10134 Tallinn, Estonia
Phone: +372 627 4135
Email: info@aki.ee
Website: https://www.aki.ee
In addition, the data subject has the right to lodge a complaint in the EU Member State where the data subject resides or works or where the alleged breach of the GDPR took place. The contact details of the EU data protection supervisory authorities can be found here.
13. Changes to This Policy
We may update this Privacy Policy from time to time. Our regular review will take place at least once per calendar year. Additional reviews will take place regarding significant changes in applicable law or in internal personal data processing. Updates will be posted to our website at www.threod.com, and significant changes will be communicated directly where possible. Amendments will enter into force upon their publication on Threod’s website, unless the amendments provide for a different deadline.